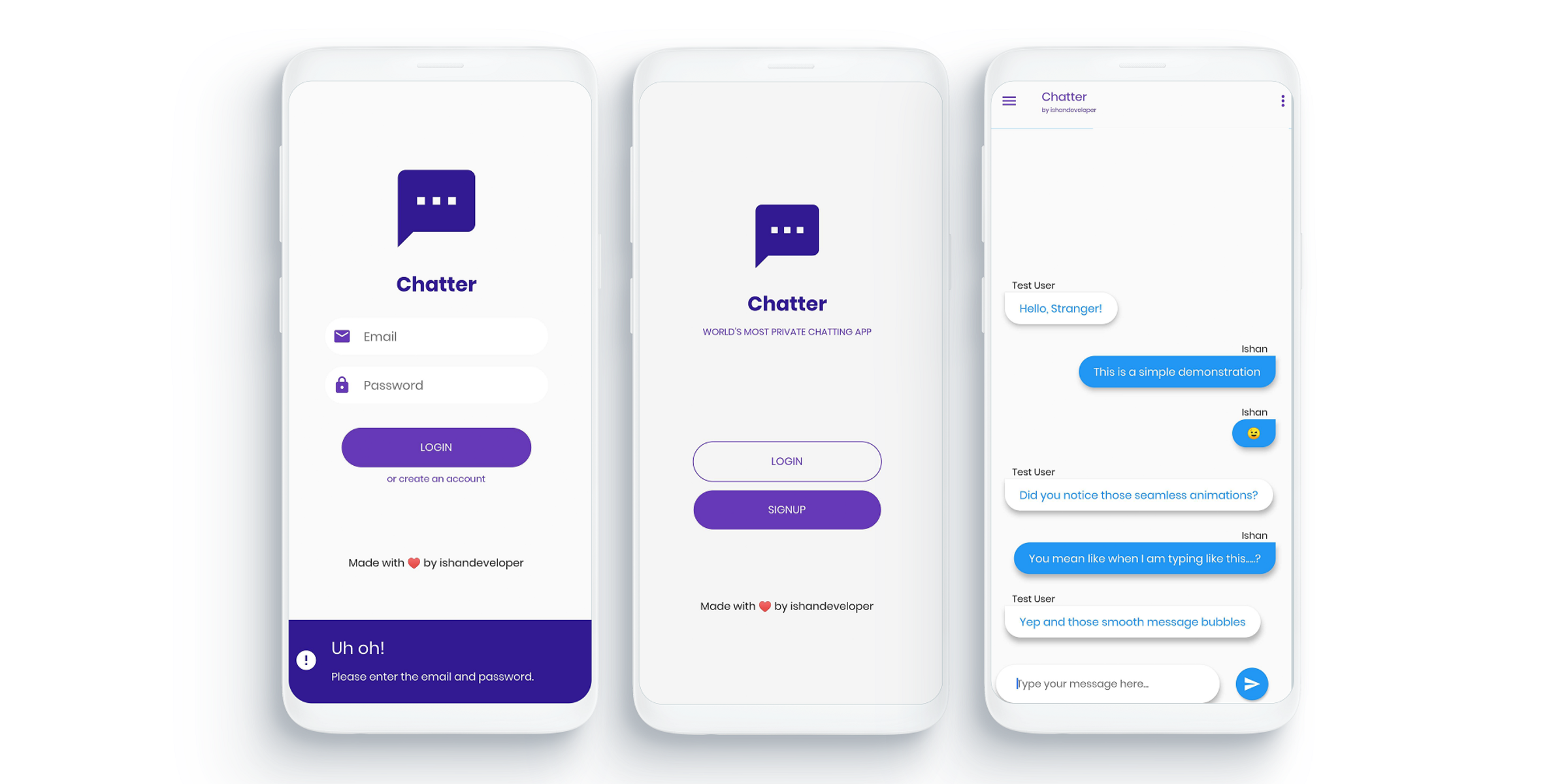
Mobile Developer
From single landing pages to a fully-blown eCommerce store,
I'll develop that fits you and your business.
Web Security
We evaluate each and every component installed in your organization’s network and cross-verify its firmware and configured protocols with the latest updates available in the market.
With this, we are able to identify best-in-class hardware and software for security purposes.
Network Security
Never let any suspicious and unauthorized user enter your network and get access to your servers.
We monitor your resources 24/7 and also install an IPS and IDS system-enabled firewall for better protection from cyber-attacks..
Penetration Testing
Our Web Security Experts test every individual IT asset to identify loopholes and examine its vulnerability in accordance with threat models and risk matrix.
Our multi-level testing methodology assists our clients to furnish their digital safety.
Linux administration
Linux administration covers backups, file restores, disaster recovery,
system security management, and storage management.
Capture the Flag
CTF in computer security is an exercise in which "flags"
are secretly hidden in purposefully-vulnerable programs or websites.
It can either be for competitive or educational purposes.